What is Phishing?
Phishing is the practice of sending fraudulent emails that look like they are from a reputable source. Phishing emails intend to persuade the recipient to reveal personal information such as login credentials or credit card numbers. This act is one of the oldest scams on the internet, and it continues to be a concern for both individuals and businesses.
According to Phishing Activity Trends Report for 2017, there were roughly 48,500 confirmed phishing attacks per month in the United States during the first half of the year. Some of the key takeaways from this report show that several hundred companies are regularly targeted, at least every few weeks, while a smaller number of companies are attacked intermittently. Over time, a few companies fall off the lists completely, only to be replaced by new and up-and-coming targets of opportunity. Phishing attacks are most common in the payment, financial, and email sectors.
Phishing attacks can be challenging to identify. Malicious attackers are smart and sophisticated in the manner that they target and attack users. They disguise their emails to look like organizations such as Netflix, Target, Bank of America, or Amazon so they can steal personal information or login credentials. These attackers design their emails to look precisely like the emails you receive from legitimate organizations. For example, some of these emails claim that “your order has shipped" and you should “check the tracking number.” Then, of course, to check the tracking, you need to “click the link below” to log in to your account. However, because you didn't order anything online recently, you want to log in and make sure something terrible hasn't happened to your account. Absentmindedly, you click the link, log in, and then without realizing it, your login credentials have just been compromised.
Phishing emails arrive in inboxes across the country every day, and spam filters do not always catch them. Luckily, you don't have to panic. This blog details both real-life examples of malicious emails and tactics you can use to identify them so you do not fall victim.
Emails that Stink
Below are some examples of emails that individuals close to our team have received recently. We didn't have to dig too hard to find these emails because they show up frequently. The best way to combat them is to first use a spam filter. However, as a reminder, spam filters and helpful tools such as Microsoft Office 365's Advanced Threat Protection don’t catch every suspicious email. New malicious phishing methods pop up every day and these tools take time to update.
Your Account Has Been Compromised Spoof
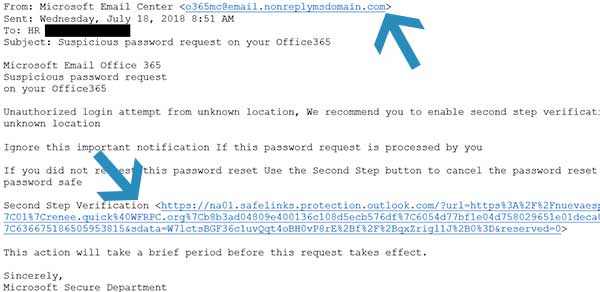
In the example above, the email looks to be from Microsoft's Secure Department. It appears to be legit, right? It says that someone attempted to log in to my Microsoft Office 365 account and that I should enable second step verification so that any unauthorized locations can be canceled. Makes sense, right? I want to protect my Microsoft Office 365 account!
Stop. Look closer. The sender's email address looks strange. It shows @email.nonreplymsdomain.com, and that doesn't look like a Microsoft domain. This is an excellent example of a phishing email. Clicking the link in that email will compromise the user’s credentials.
Your Account Needs Confirmation Spoof
One of our employees received this email. It appears to be from someone who states that his Bank of America account would be limited over 24 (hours) if he did not confirm the account by logging into his account through the email.
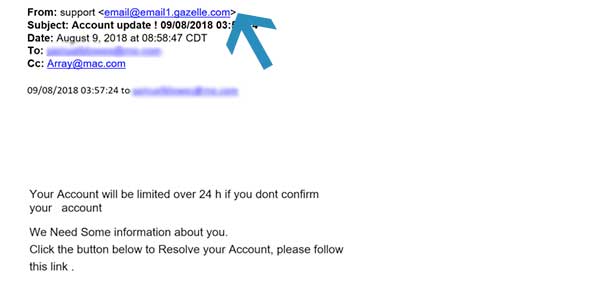
The email above is an example of using a threat to coax the recipient into clicking a link and entering their credentials.
Stop. Look closer. Again, the sender's email address looks strange. It shows email@email1.gazelle.com, and that doesn't look like a Bank of America domain. This is another excellent example of a phishing email. Clicking the link in that email will compromise the user’s credentials.
Someone Needs You to Buy Gift Cards Spoof
Scam artists use phishing emails to entice people to do all kinds of things. These scammy emails can look a little different than the typical phishing email, but they are just as devastating.
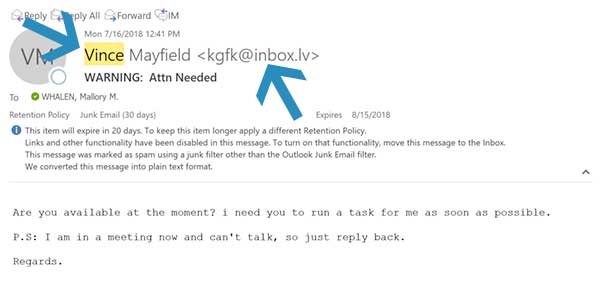
The example above came to the inbox of our Director of HR with the sender posing as Vince Mayfield, our CEO. This email asks for a simple response. In the email, the sender tells Mallory that he is busy and needs her to reply to the email. What is occurring here is that someone on the other side of that email is waiting for Mallory to respond. If she chooses to email back, the sender would then email her again and ask her to purchase a specific dollar amount of gift cards, scratch off the back, take a picture, and send it to them. Still posing as Vince, they would then claim that they are very busy and are in meetings and to please communicate only through email.
Luckily, Mallory stopped and looked closer and did not respond. Because Vince is our CEO, we know that he does not have an email address with the
@inbox.lv domain. Stopping to look at both the name and the email address is very important because any email account name can be changed in the account settings. Pretty sneaky.
Reputable Organization Invoice Spoof
Viruses and ransomware can easily be spread through phishing emails as well.
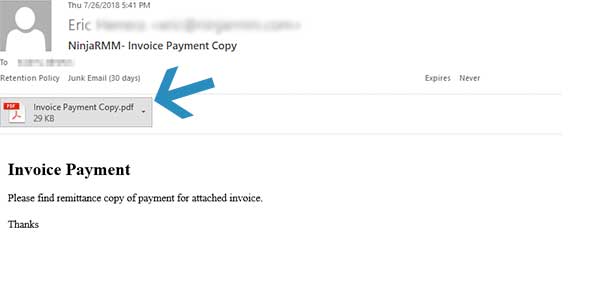
This example is especially concerning because it comes from a reputable source. Anyone doing business with this organization may see this email and consider that the attached PDF is legitimate.
Stop. Look closer. If you don't typically receive invoices through email or if you pay for services through a web portal, that is the first flag that should make you stop and think. If you are unsure whether or not an attachment is safe to open, you should not open the email at all. Again, stop, look closer, and think before clicking.
We Know Each Other, So Open the Attachment Spoof
This example email came to another Bit-Wizards employee directly, and it is a powerful example of a malicious email. When the employee received this email, they realized that they did not know the sender.
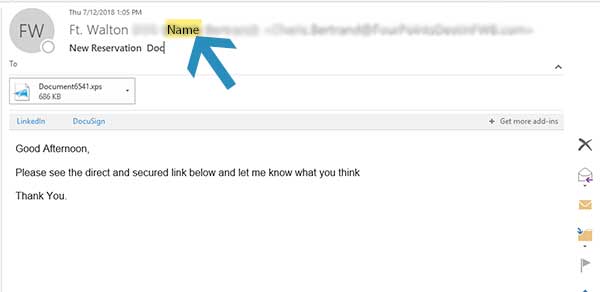 The employee stopped and looked closer. T
The employee stopped and looked closer. They took the time to look into the email a little further and found out that their contact information is saved in this person’s email. The hacker who compromised the account sent emails to the entire contact list of the person whom they hacked. So, for this example, the email did come from a legitimate account, but it is still malicious. Because our employee recognized that they didn’t know the person, they immediately flagged the email and trashed it. They also took the time to locate this person on LinkedIn to inform her of the situation.
Always, stop and think – but then what?
If it looks phishy and smells phishy, then it probably is phishy. Clearly, you should always stop and think. However, what is the next step? It is more straightforward than you might think. You can start by asking yourself the following questions to help eliminate threats before they can cause you, your business, or your contacts harm.
- Why am I receiving this email?
- What is it asking me to do?
- What is the sender's email address (not just the sender's name)?
- When hovering the cursor over the link (whether it's text or an image) what is the website URL displayed? This is the link you will visit if you click.
Staying safe online is part of everyday life. We must all pay attention to what we are doing online. Email is no different. If you think your business needs to improve your overall
IT security,
please get in touch.