Setting up a Site-to-Site VPN Tunnel on an ASA 5505 is pretty snappy if you use the VPN Wizard.
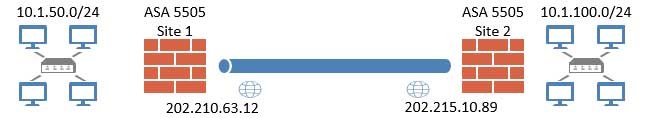
Here is our test lab configuration.
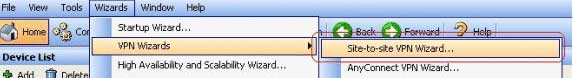
First let’s start that wizard! On Site 1 ASDM you'll find it under “wizards” at the top of the ADSM window.
The next page is really just to make sure you understand your setting up a site-to-site VPN, an "introduction" to set up.
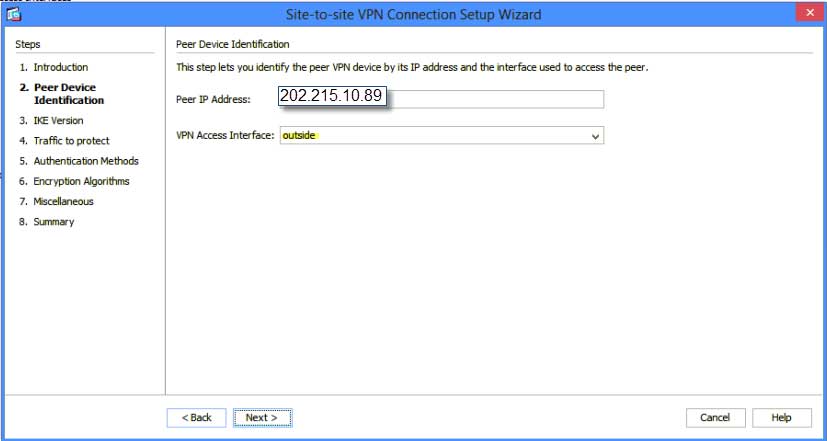
Click “next” and it's time to identify the peer or remote IP of the ASA on the other side of the tunnel we are connecting to. In this case: Site 2 or 202.215.10.89
The Access Interface is outside, because that’s where the VPN is initiating and terminating.
On IKE Version I strongly suggest only version 2.
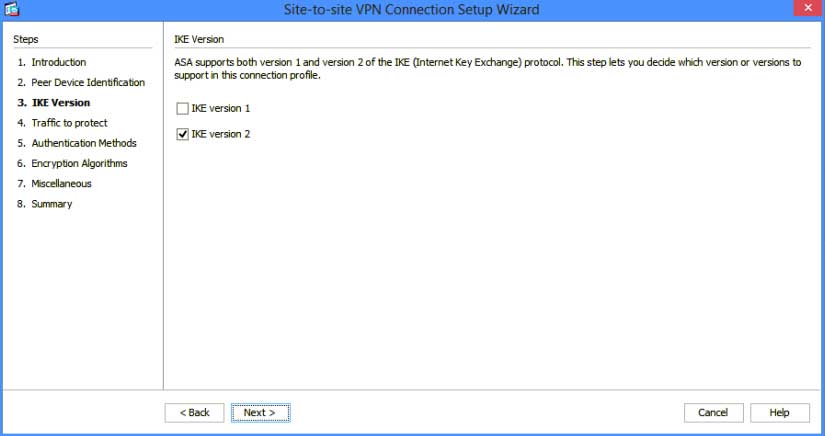
Traffic to protect is where you identify what networks are allowed to talk with one another. You can get really granular with these policies in the Command Line Interface CLI. Do not change the Radio button to IPv6
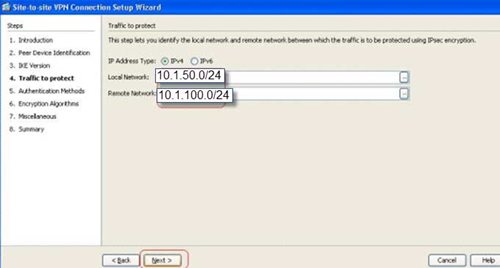
In our case, our local Subnet is 10.1.50.0/24 and the remote subnet is 10.0.100.0/24 then click next.
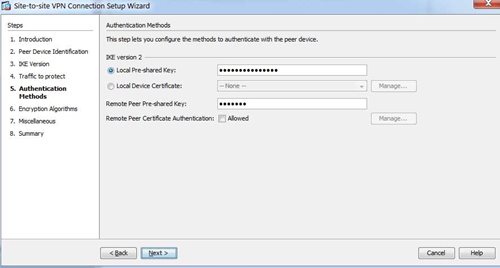
On authentication, you can use a pre-shared key for your lab. You may have higher security requirements in which you mix with certificate mode, but we don’t need it for our lab.
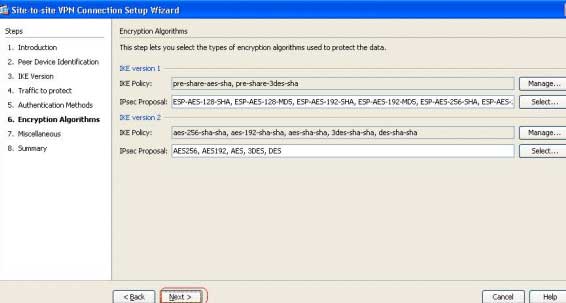
Next, leave the default for “Encryption Algorithms” and click “next.”
Don't click anything on Miscellaneous other than "Exempt ASA side host/network from address translation (inside)” in the drop down.
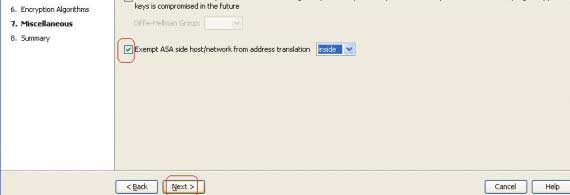
Now click “finish”, then repeat this process on the other ASA with the reverse configuration.
And to check and make sure your tunnel is up, click on “Monitoring” on the top ribbon then “VPN” in the left admin window to see active sessions!
You are all done!