
4 Types of Phishing Attacks to Know
How common phishing attacks use unique methods to steal information.
Phishing attacks are one of the most common cyber threats, and they come in different varieties. Each approach uses unique tactics to convince victims to share login credentials, download malware, and other similar goals. Learn about how phishing works, which techniques are most common, and how you can spot them before it’s too late.
What is phishing?
TechTarget defines phishing as a scheme in which a bad actor impersonates a legitimate business or organization using a fake email, website, or other digital medium. Each approach involves social engineering that prioritizes psychological and emotional manipulation over technical skills. Brian Schlechter, Director of IT at Bit-Wizards, says those who use phishing attacks can be equated to digital con artists.
“You can be a hacker even if you don’t know anything technical as long as you can convince someone,” he says. “It’s like being a scammer who has a more widespread attack base to gain more revenue using less effort.”
What is the goal of successful phishing?
No matter how it’s executed, a phishing attack aims to steal information or coerce someone into sharing it. Whether it’s personal banking details or corporate login credentials, hackers want information or access they can leverage to make a profit. Because of the usual scale of phishing attacks, Schlechter explains that even a tiny portion of successes can lead to widespread damage.
“If someone sends out a million phishing emails and only 100 respond, that’s less than a 1% response rate,” he says. “Even with such a small margin of success, that could put tens of thousands of dollars in a hacker’s pockets.”
What are some common types of phishing?
Phishing takes many forms, and different organizations identify various types. For example, Fortinet recognizes 19 types of attacks, while Cisco acknowledges seven main buckets. Schlechter and the team at Bit-Wizards believe everyone should learn about these four increasingly common types of phishing attacks and their variants to protect their personal and professional livelihoods.
1. Spear phishing
A spear phishing attack is directed at a specific individual or business. Attackers gather information from company websites, social media platforms, and other public resources to learn about their potential targets. Once they’ve collected enough, they add personal details to their attacks to make them seem more convincing.
A subset of spear phishing is whaling, an attack that targets a business or organization’s executives. Whaling involves more detailed research to make a message as convincing as possible, which is often easy since plenty of information is publicly available. These attacks aim to convince victims that another executive is requesting an authorized payment, which goes to the hacker.
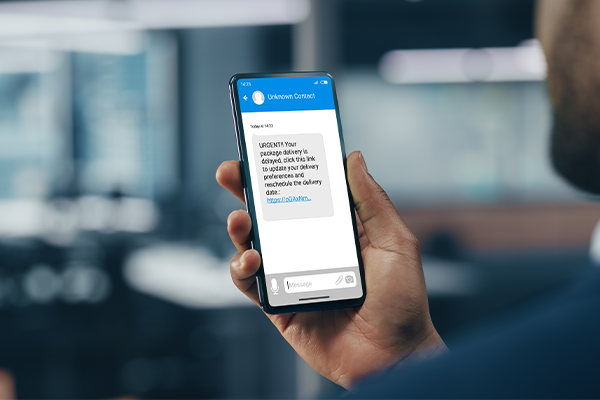
2. SMS phishing
SMS phishing, also known as smishing, aims to convince people to share information or click malicious links using text messages and other messaging apps. Attackers usually pose as government agencies, banks, or other organizations that collect payments from people. Smishing often leverages fake consequences a victim will suffer for a missed payment.
3. Angler phishing
Where traditional phishing uses emails, angler phishing attacks use social media to compel people to share information. Attackers look for people commenting on a brand’s posts about a negative experience. Once they identify potential victims, they set up a fake account of that brand and pose as customer service agents offering compensation or discounts.
Similar methods are used in website spoofing attacks, where someone creates a fake version of a legitimate website that many people visit. The web address looks identical at first glance but has minor changes like an extra letter or period. Instead of just using social media, attackers send the spoofed website in emails and other messages to steal information.
4. Evil twin phishing
Also called an evil twin attack, evil twin phishing is a less-involved attack that uses a malicious Wi-Fi network that looks like a legitimate one. Attackers often go to public places like airports and coffee shops, identify official networks, and create duplicates with slight name changes. Once people connect to the fake Wi-Fi, their browsing history, passwords, and other personal information can be easily stolen.
How can I spot a phishing attempt?
Schlechter says you should examine these aspects of a message to gauge whether it’s a potential phishing attack:
- Relevance—Does the message come from a company or person you know?
- Introduction—Is the message personalized or a generic “Dear sir/madam?"
- Tone—Does the message seem overly official or too casual?
- Grammar—Is the message written with spelling or grammatical errors?
- Urgency—Does the message demand you take immediate action to avoid consequences?
- Email domain—Does the email address domain name match the company or organization?
- Attachments—Are there any unexpected links or files included in the message?

Any combination of these flags in an email should at least make you pause and consider if it’s legitimate or malicious. Many of these aspects are usually present in phishing emails, even though some are more convincing than others.
Are phishing attempts easy to spot?
While phishing attack markers can be hard to miss, it’s vital to note that AI enhances the risks by making these attempts more credible. Bad actors can use generative AI to write flawless messages or even alter someone’s voice to commit vishing attacks. In any case, Schlechter stresses that it’s highly crucial to have a healthy sense of suspicion.
“When in doubt, you can always verify a message’s request without clicking potentially harmful content,” he says. “Go directly to a company or organization’s website to verify if a deal or demand is legitimate.”
What can I do if I fall for a phishing attack?
In the event you click a suspicious link in a phishing email, Schlechter recommends following these four steps:
- Close all your programs and browsers
- Shut down the device you were using
- Change your account password on another device
- Seek help from an IT professional
These steps cover the basics, but there’s usually more to do if phishing happens on a business account. If you work in a regulated industry like healthcare, local government, or legal services, you may need to follow additional steps to protect your company and customers. When in doubt, work with your internal IT department to follow the correct procedures.

Can phishing attacks be prevented?
Nothing can stop an attacker from using phishing to target you as a future victim, but these measures can help you prevent them from getting close enough to work:
- Multifactor authentication (MFA)—Use MFA to make it harder for phishing attempts to succeed with compromised passwords alone.
- Email filters—Configure settings in your email to flag or quarantine messages that are potential attack attempts.
- Antivirus software—Use programs that can identify and get rid of malicious links and files before you interact with them.
- Access management—Only give employees access to programs and files they need for their job to minimize the impact of security failures.
- Business policies—Set rules for your organization to properly verify requests for information, access, and payments.
- Employee training—Provide regular opportunities for your team to learn how to spot, avoid, and report phishing.
Can an MSP protect my business from phishing?
Phishing attacks are just one of the many ever-evolving cyber threats that put businesses at risk. Many learn cyberattack lessons from first-hand experience, but it doesn’t have to happen to you directly in order to understand the key takeaways. Instead, working with a managed service provider (MSP) can help your company follow proactive IT security practices.
When you need a team of IT professionals who take the security of your business as seriously as their own, Bit-Wizards is here to help. With our Managed IT Services (MITS), your company’s technology can run safely without compromising on efficiency. Our Wizards take a multilayered approach to security, ensuring your business and operations are prepared for worst-case scenarios while planning for future successes.
Ready for secure, reliable IT? Get in touch.